
2023-11 Fileless Cyber Attacks
How It Works
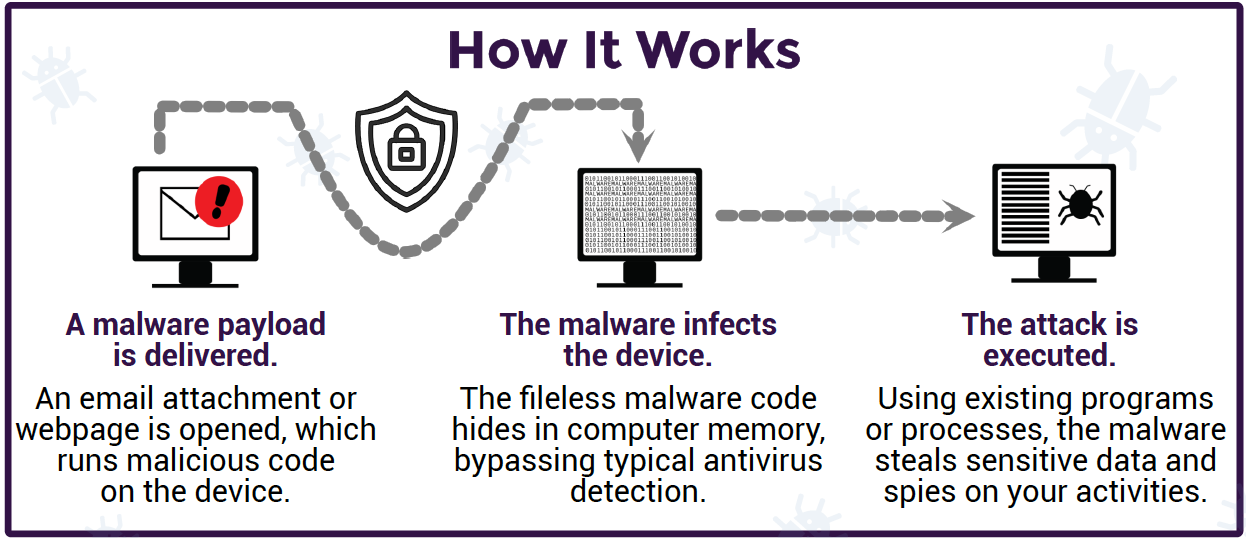
How to Protect Yourself
- Keep your devices and applications updated. Only install applications from trusted sources. For Terrapin clients, we monitor and automate this as part of the security package for your systems. Remember to reboot your computer weekly, so that any pending updates that require a reboot can get installed.
- Do no click on links or attachments in unexpected emails. Beware of phishing and vishing attempts. It is a good practice to not trust any email until verified. If you need help, we are happy to help in that process.
Vigilance is key. Fileless attacks often start with social engineering, and take advantage of systems that do not have current updates installed. Your watchfullness is a vital part of the security process to protect yourself, your company and your clients.
